Proxiyum is a web-based proxy service that enhances online privacy, security, and unrestricted internet access by acting as a secure intermediary between a user’s device and the internet. It allows users to browse websites anonymously, bypass digital restrictions, and protect their real IP address by routing traffic through protected proxy servers. This architecture creates a safer digital environment where users can access global content without direct exposure to tracking systems or surveillance tools.
- How Proxiyum Works as a Secure Intermediary
- IP Masking and Digital Identity Protection
- Bypassing Geo-Restrictions and Network Filters
- Web-Based Architecture and Accessibility
- Security Infrastructure and Data Protection
- Use Cases Across Digital Ecosystems
- Direct Browsing vs Proxy-Based Browsing
- Ethical Use and Digital Responsibility
- FAQs
- Conclusion
In today’s data-driven online world, digital privacy, identity protection, and content accessibility are no longer optional. Users face geo-blocking, content filtering, network restrictions, and aggressive data tracking. Proxiyum addresses these challenges through secure traffic routing, identity masking, and unrestricted access, offering a practical solution for privacy-focused users, professionals, and organizations seeking safer digital freedom.
How Proxiyum Works as a Secure Intermediary
Proxiyum operates through a proxy-based communication model that separates the user from direct contact with the internet. When a user enters a website address into the platform, the request is sent to a proxy server instead of the destination website. The server forwards the request, retrieves the content, and delivers it back to the user securely.
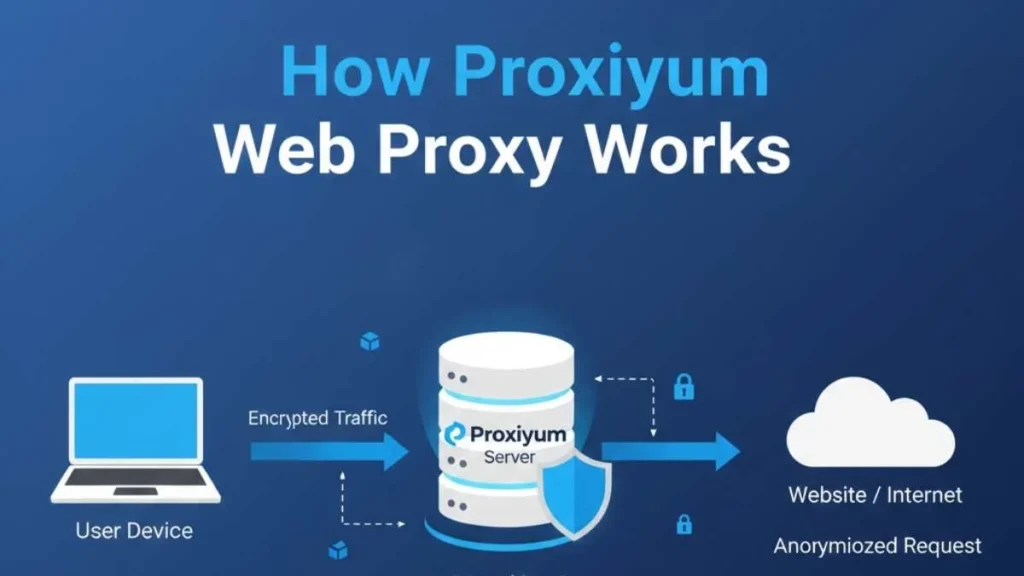
This indirect connection structure creates a digital buffer that protects user identity, hides real IP addresses, and prevents direct tracking. External websites only interact with the proxy server, not the user’s device. This model significantly reduces exposure to tracking scripts, profiling systems, and data harvesting technologies.
IP Masking and Digital Identity Protection
A user’s IP address reveals location data, network information, and browsing patterns. It is one of the most commonly used tools for digital tracking and behavioral profiling. By replacing the user’s real IP address with a proxy IP, Proxiyum prevents websites and platforms from identifying or tracking the user’s actual digital identity.
Bypassing Geo-Restrictions and Network Filters
Digital restrictions exist at multiple levels, including geographic content blocking, institutional firewalls, and network-level censorship. Many platforms restrict access based on country, region, or local regulations, limiting the free flow of information.
Proxiyum enables access to restricted platforms by routing traffic through servers in different locations. This makes users appear as if they are browsing from another region, allowing them to unlock region-locked content, access blocked platforms, and retrieve restricted information
Web-Based Architecture and Accessibility
Unlike traditional proxy tools that require software installation or system-level configuration, Proxiyum is fully web-based. Users can access it directly through a browser interface, making it compatible across devices, operating systems, and network environments.
This structure provides:
- No installation requirements
- Device flexibility
- Cross-platform compatibility
- Quick setup access
- User-friendly navigation
The simplicity of access ensures that privacy tools are available to both technical and non-technical users without complex configurations.
Security Infrastructure and Data Protection
Security is a core structural component of Proxiyum. The proxy routing model reduces direct exposure between users and external servers, lowering risks associated with cyberattacks, data interception, and malicious tracking.
Core security benefits include:
- Secure traffic routing
- Reduced exposure to malware sources
- Protection from direct server attacks
- Encrypted communication pathways
- Controlled server environments
This approach aligns with global cybersecurity best practices and supports safer digital interactions.
Use Cases Across Digital Ecosystems
Proxiyum serves multiple user groups across industries and digital environments.
Education and Research
Students and researchers use proxy services to access restricted academic journals, global libraries, and international databases.
Business and Digital Professionals
Professionals rely on anonymous access for market research, competitor analysis, SEO research, and global content audits.
Journalism and Media
Reporters and analysts use secure browsing to access information in restricted environments while protecting their identities.
Travel and Remote Work
Remote workers and travelers maintain access to region-specific platforms while abroad.
Personal Privacy
Every day, users protect personal data, browsing habits, and digital identity from tracking systems.
Direct Browsing vs Proxy-Based Browsing
| Feature | Direct Internet Access | Proxy-Based Access |
| IP Protection | No | Yes |
| Identity Masking | No | Yes |
| Geo-Restriction Bypass | No | Yes |
| Privacy Level | Low | High |
| Data Exposure Risk | High | Reduced |
| Anonymity | None | Strong |
| Access Control | Restricted | Flexible |
Ethical Use and Digital Responsibility
Ethical proxy usage focuses on privacy protection, freedom of information, and personal security. Responsible services like Proxiyum are designed to protect users, not enable misuse. Ethical digital access supports transparency, safety, and lawful online behavior.
Trustworthy proxy services prioritize user protection, responsible data handling, and transparent operational practices. This ethical framework builds long-term trust, credibility, and digital responsibility.
FAQs
Is Proxiyum safe for public Wi-Fi networks?
Yes, it adds a security layer that reduces exposure on public connections.
Can Proxiyum improve online privacy without software installation?
Yes, it is fully web-based and requires no downloads.
Does Proxiyum support cross-device browsing?
Yes, it works across devices and operating systems.
Conclusion
Proxiyum delivers a reliable web-based proxy solution that enhances privacy, strengthens security, and expands access to global content. By acting as a secure intermediary, it protects user identity, masks IP addresses, and removes digital barriers that limit information access.
In a digital world shaped by surveillance, restrictions, and data exploitation, platforms like Proxiyum restore control to users. Through secure browsing, anonymous access, and unrestricted connectivity, it supports a safer, more open, and more ethical internet experience for individuals, professionals, and organizations worldwide.








